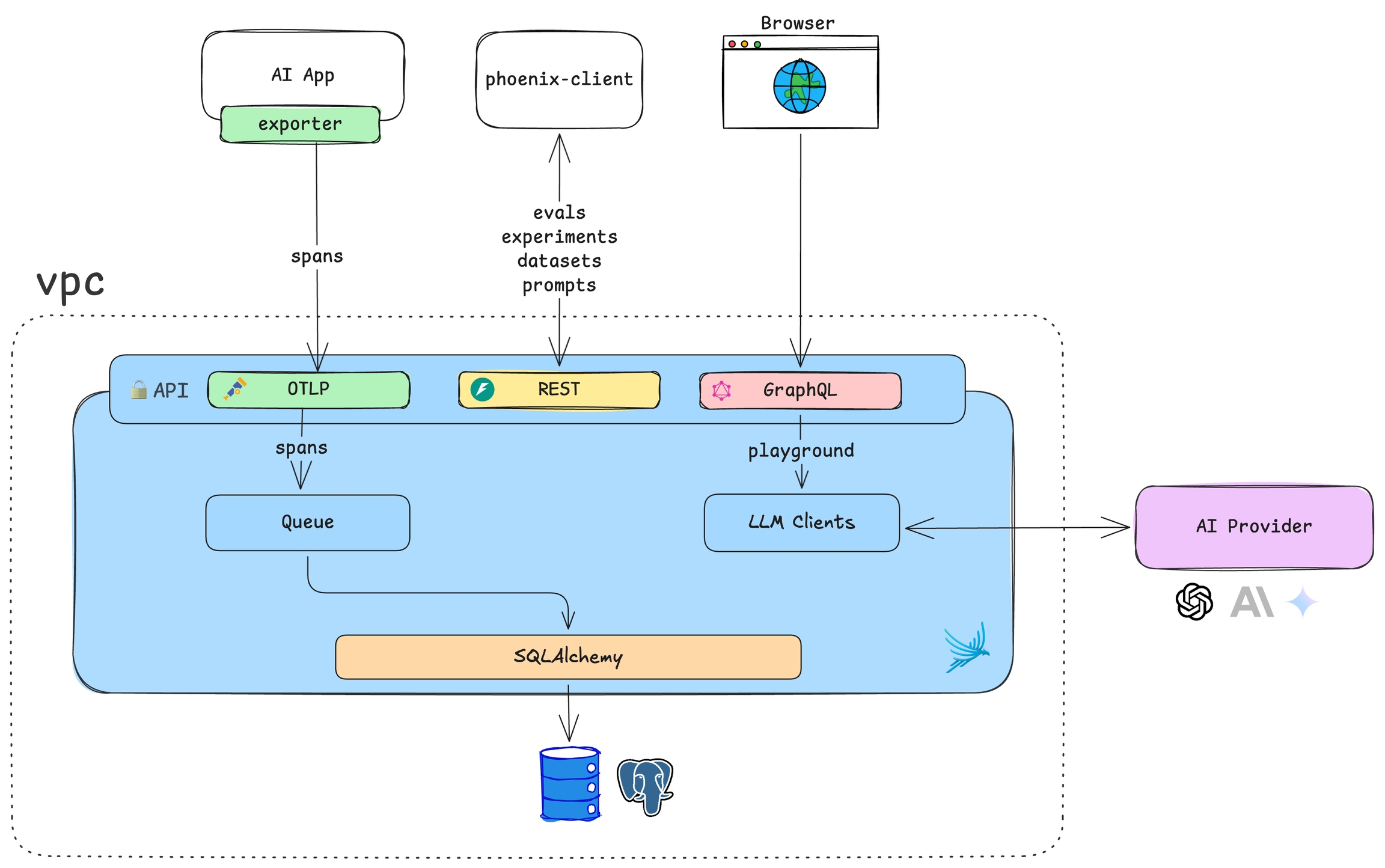
How to self-host a Phoenix instance
Phoenix is a containerized application designed to collect and analyze traces from your LLM or AI application. It operates with a SQL database backend and provides a robust tracing UI. By default, Phoenix uses SQLite for storage, but it can be configured to use PostgreSQL for production deployments.
By default, Phoenix uses SQLite, storing data in ~/.phoenix/ or the directory specified by the PHOENIX_WORKING_DIR environment variable. This allows for simple deployments using a volume mount, making it easy to get started without additional database setup.
For production and scalable deployments, Phoenix supports PostgreSQL. Configure the PHOENIX_SQL_DATABASE_URL environment variable to connect Phoenix to your PostgreSQL instance.
Phoenix can be deployed using several methods, including Docker and Kubernetes. Choose the option that best fits your infrastructure and operational requirements.
See available ports to run Phoenix
Customize Phoenix using environment variables
Setup authentication
Configuring OAuth2 identity providers
This table lists the images we publish that can be used to run Phoenix.
arizephoenix/phoenix:latest
Latest released version of Phoenix using root permissions.
arizephoenix/phoenix:latest-nonroot
Latest released version of Phoenix using nonroot permissions. Ensure the image has the required filesystem permissions before using.
arizephoenix/phoenix:latest-debug
Latest released version of Phoenix using a debug base image.
arizephoenix/phoenix:version-X.X.X
Build for a specific release version using root permissions.
arizephoenix/phoenix:version-X.X.X-nonroot
Build for a specific release version using nonroot permissions.
arizephoenix/phoenix:version-X.X.X-debug
Build for a specific release version using a debug image.
Docker
How to deploy Phoenix using Docker
Kubernetes
How to deploy Phoenix on K8S
