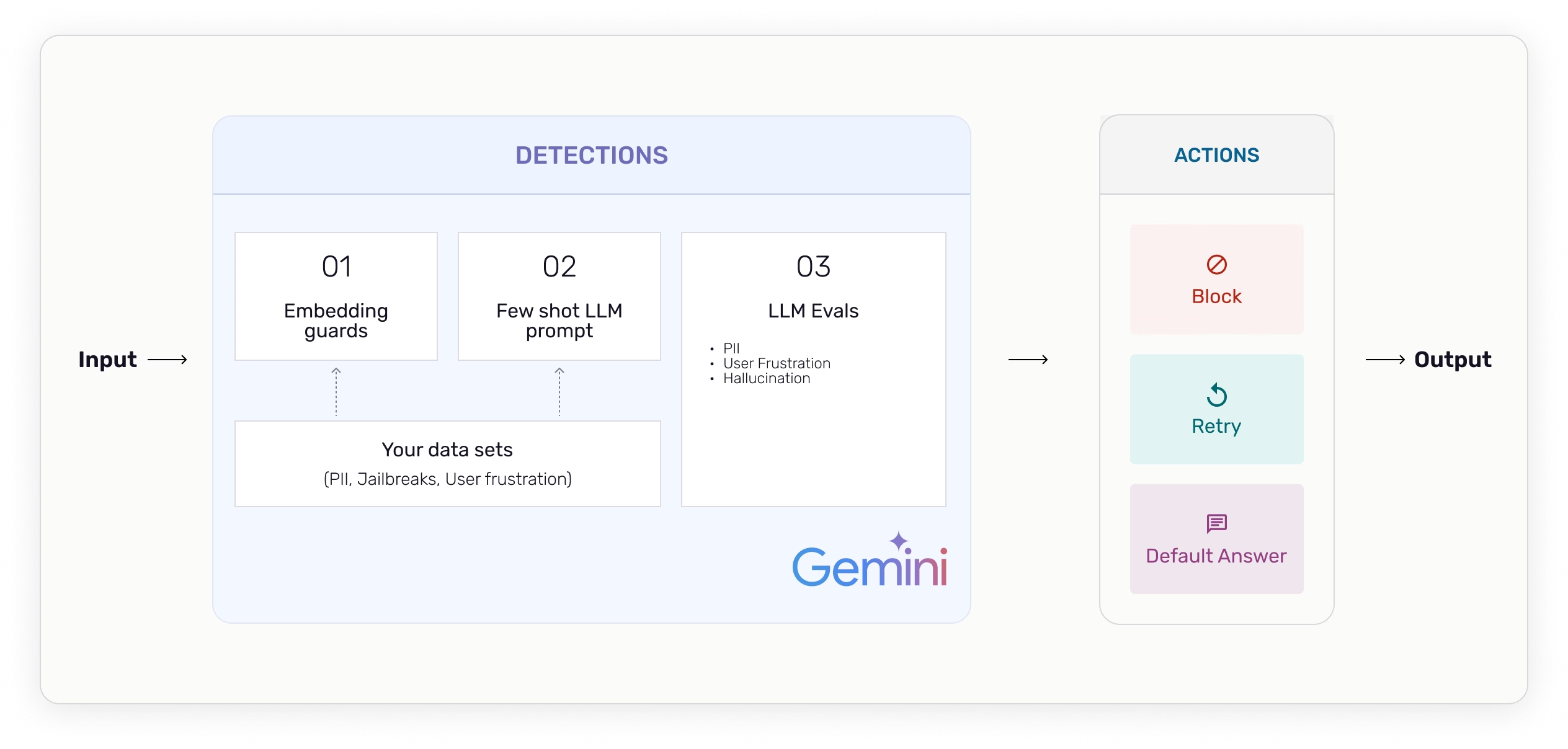
Arize guardrails can be configured using custom datasets and a fine-tuned Vertex AI Gemini model for embeddings guards, few-shot LLM prompt, and LLM evaluations.
Powering the Next Generation of AI with Arize + Google Cloud
A seamless integration to scale, monitor, and optimize AI with confidence.

Unified AI Engineering Platform to Make AI Work
End-to-end visibility for AI at scale.
Arize and Google Cloud empower teams to track, diagnose, and optimize LLMs and AI agents throughout development and deployment.
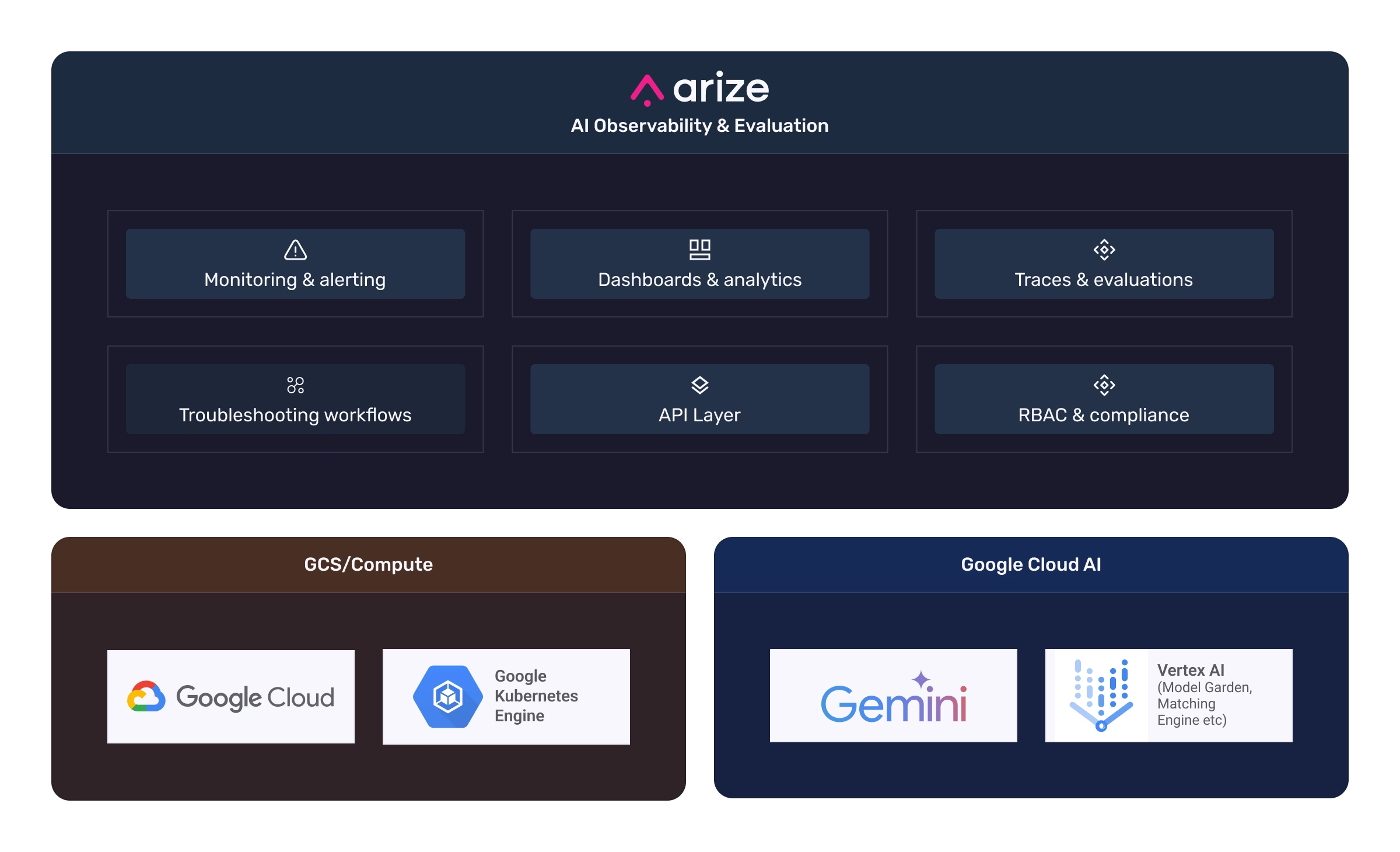
Natively integrated with Vertex AI.
Arize fits seamlessly into your stack for real-time debugging, tracing, and evaluation.
How Arize works with Google Cloud
Build successful and expanded GenAI use-cases with seamless integration with Vertex AI & Gemini.

Why use Arize and Google Cloud together
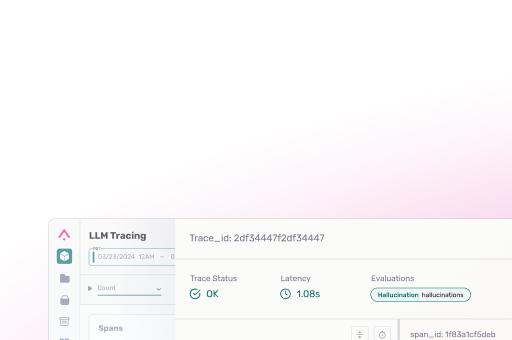
Operationalize LLM evaluation with Vertex AI API + Arize
Scale prompt testing and evaluation using Gemini through Arize’s integrated workflows—complete with dynamic dataset curation, labeling tools, and guardrails.
Scale LLM evaluation with Gemini and Arize
Run automated evaluations across your telemetry data using Gemini or your own custom logic.
Full-stack visibility without lock-In
Arize and Google Cloud support flexible, open architectures with built-in tools for debugging, monitoring, and stakeholder reporting.
Safeguard Your Business with Arize and Vertex AI API Serving Gemini
Start your AI observability journey.
Get in touch with our team of AI observability experts to see how Arize and Databricks can work together for your business.
Evaluation Driven Development
Purpose-built tools and workflows that streamline performance improvement iteration cycles
Test Changes As You Build
Prompt template versioning and a prompt playground enable testing as you go, along with the ability to replay use cases in production.
Quickly Find and Curate Datasets
AI-driven search and embeddings similarity search eliminates manual data curation and annotation in your daily workflow.
Guardrails to Protect Your Business
Dynamic data used for detection of activities such as jailbreaks, PII leaks, or user frustration – then respond with a corrective action.
Continue the conversation