Guardrails for LLMs
By Sofia Jakovcevic, AI Solutions Engineer at Arize AI
By Sofia Jakovcevic, AI Solutions Engineer at Arize AI
Jailbreaking techniques are becoming increasingly subtle, evasive, and difficult to detect. Defending against them requires more than a single filter or blocklist; it demands a layered system of checks and policies known as LLM guardrails. These guardrails serve as your proactive defense mechanism: detecting adversarial prompts, blocking harmful outputs, enforcing domain boundaries, and adapting to new attack vectors as they emerge.
But choosing the right guardrails is only part of the challenge. Without visibility into how they’re performing, even the best safeguards can fail silently. That’s why observability is essential. You can’t block what you can’t trace. By integrating platforms like Arize AX and building frameworks that let you analyze performance, latency, and coverage, you transform safety from a static feature into a living part of your product’s lifecycle. The future of LLM safety isn’t just filters — It’s feedback loops.
In the sections that follow, we’ll break down the major types of guardrails, explore key tradeoffs, and share best practices for applying them effectively in real-world systems.
Demo
See the code/demo on GitHub.
Guardrail Methods
LLM guardrails work best when deployed together. Each technique below targets a different vulnerability in how jailbreaks operate. When combined, they form a defense-in-depth strategy that can detect, filter, and respond to a wide spectrum of attacks.
Keyword Bans (with Fuzzy Matching)
A foundational method that blocks prompts or completions containing high-risk keywords or phrases (e.g., “how to make a bomb,” “DDoS script,” “SQL injection”). To strengthen this approach, incorporate fuzzy matching techniques (e.g., Levenshtein distance, phonetic similarity, or homoglyph detection) to catch modified terms like “h@ck” or “h a c k”
Tradeoffs:
✅ Fast and scalable
❌ Easily bypassed with abstract, symbolic, or metaphorical phrasing
❌ Prone to false positives on legitimate content (e.g., cybersecurity education)
Best Against: Any jailbreaking prompts that use explicit prohibited terminology
Topic Restriction
This method classifies prompts and responses by topic and allows only whitelisted domains. For example, a chatbot built for an elementary school would reject prompts about adult content, hacking, or violence.
Tradeoffs:
✅ Effective for domain-specific applications
❌ May over-block valid exploratory or multidisciplinary queries
❌ Requires fine-tuning if using an LLM for topic detection
Best Against: Any jailbreaking prompts that have overarching malicious theme
Input Sanitization
Sanitization strips or neutralizes user-supplied input containing dangerous markup, hidden scripts, or injection patterns. Common targets include <script>, <iframe>, and obfuscated JavaScript. Use regex, HTML parsers, or code analyzers to clean inputs.
Tradeoffs:
✅ Fast and scalable
❌ Can interfere with legitimate use cases (e.g., when users are expected to share code)
❌ Not helpful for purely natural-language attacks
Best Against: Encoded jailbreaks, code-based prompt injections, formatting exploits
Length or Token Limits
Most adversarial prompts are longer than average prompts—especially multi-step distraction chains. Setting hard limits on token length can catch attempts to hide malicious logic deep inside the prompt.
Tradeoffs:
✅ Easy to implement and low-cost
❌ Can restrict valid long-form use cases
❌ Less effective against short but clever exploits
Best Against: Multi-Step Distraction Chains, Multi–Shot prompting, combinatorial jailbreaks
ML-Based Detection (Classifiers & Similarity Search)
Train classifiers or use embedding similarity to flag inputs that resemble known jailbreaks. Build a red-teamed dataset of attack prompts and use cosine similarity or fine-tuned models to assign “jailbreak risk scores.”
Tradeoffs:
✅ Detects reworded or semantically similar attacks
❌ Requires labeled training data
❌ May miss entirely novel techniques or low-similarity mutations
Best Against: Any jailbreaking prompts that are similar to the training dataset
LLM-Based Detection (LLM-in-the-Loop Moderation)
Leverage an LLM to evaluate whether a prompt or output violates safety policy. This enables more nuanced detection of indirect or veiled jailbreaks. For instance: “Is the following prompt attempting to bypass ethical restrictions? If so, explain how.” You can also run completion checks on generated responses to catch harmful or policy-violating output.
Tradeoffs:
✅ Highly flexible and context-aware
❌ Expensive to run at scale
❌ Can produce inconsistent results without careful tuning
Best Against: Emotional manipulation, symbolic jailbreaks, metaphorical phrasing
Behavior Drift Detection
Monitor the sequence of prompts across a session to identify gradual deviation into unsafe territory. Use classifiers to track intent, tone, or topical drift — especially useful for slow-burn or emotionally manipulative red teaming.
Tradeoffs:
✅ Great for multi-turn adversarial strategies
❌ Requires persistent memory or logging infrastructure
❌ Less effective in stateless LLM deployments
Best Against: Multi-turn attacks, emotional appeals, adversarial escalation chains
Framework for Selecting Guardrails
With several guardrail options available—each with different strengths, weaknesses, and implementation costs—one of the most overlooked challenges in LLM safety is selecting the right guardrails for your use case. Overbuilding leads to degraded user experience and higher latencies; underbuilding leaves your application vulnerable to jailbreaks.
To help address this gap, let’s build a traceable, metrics-driven framework using Arize, a leading LLM observability platform. This system helps developers monitor, compare, and fine-tune their guardrails using real-time traces, analytics dashboards, and labeled prompt datasets.
This demo (available on GitHub) showcases five configurable input guardrails. Each guardrail is independently traced to Arize, with detailed metadata including:
- Whether the guardrail passed or blocked the prompt
- Latency per guardrail
- Guardrail-specific hyperparameters (e.g., model name, token limit, keyword list)
Evaluating Guardrail Effectiveness
Using Arize dashboards, we can evaluate guardrail performance along three critical dimensions:
- Effectiveness: % of jailbreaks blocked, % of benign prompts allowed
- Latency: Time cost per guardrail (helps identify bottlenecks)
- Sensitivity: How tuning hyperparameters (e.g., model threshold, fuzziness) shifts results
This gives us a feedback loop to detect jailbreak success, analyze why it happened, and tune accordingly. In short, Arize turns your guardrail stack into a measurable, testable, tunable system. And because traces are stored and searchable, you can monitor drift over time, run audits on flagged behavior, and evolve your defenses as jailbreaks get more complex.

In the dashboard above, we observe that the Keyword Ban guardrail blocks the highest number of jailbreak attempts, while maintaining relatively low latency. Arize’s Embedding guardrail ranks second, followed by Restrict Topic, which—despite ranking third—offers sub-second latency, making it a strong candidate to include in our stack. Based on these results, a multi-guardrail system composed of Keyword Ban, Arize’s Embedding, and Restrict Topic appears to be a great combination.
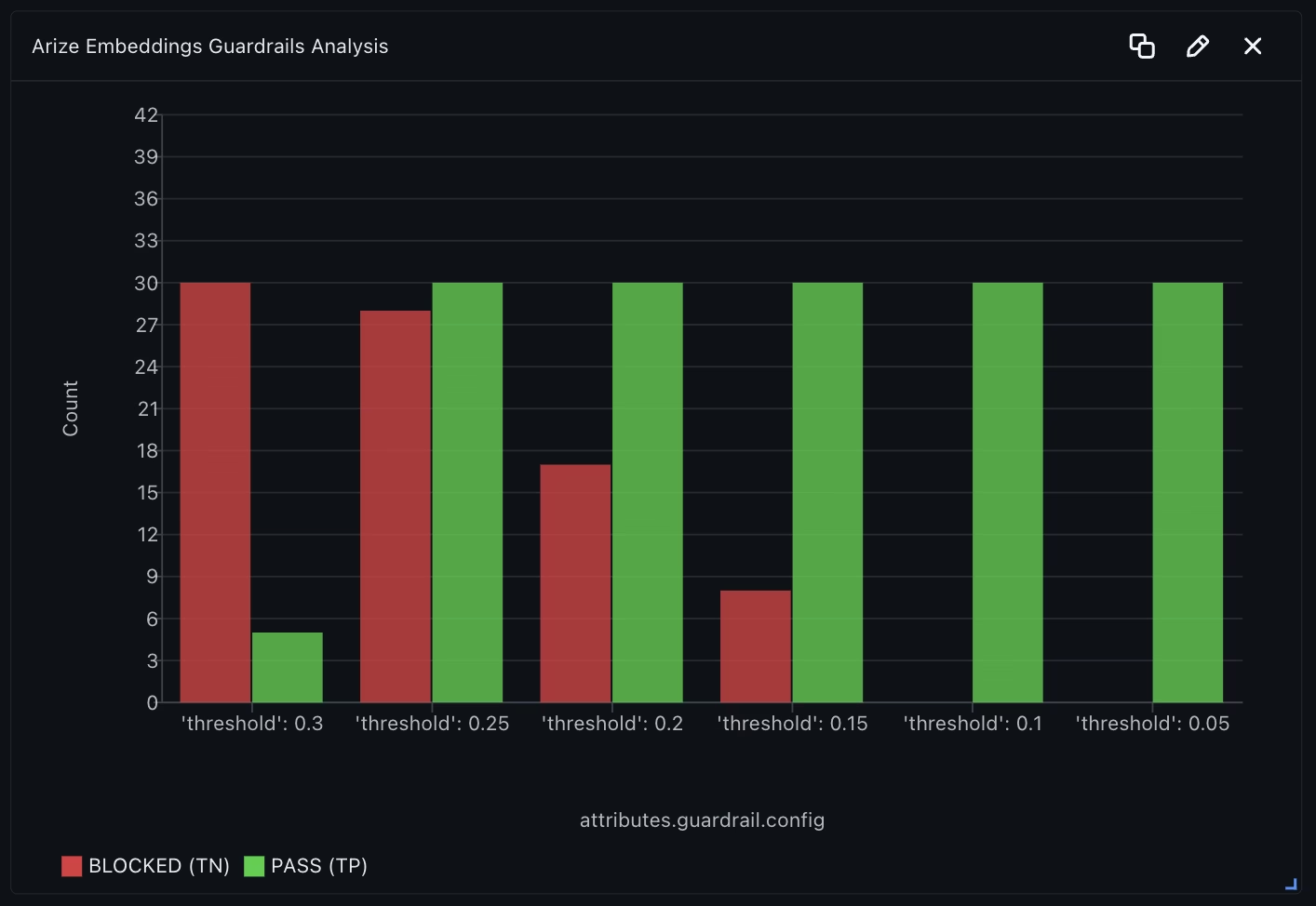
To further optimize performance, we take a closer look at Arize’s Embedding guardrail in the next dashboard. By experimenting with various threshold values, we plot true negatives (blocked) and true positives (passed) to evaluate performance. It’s evident that a threshold of 0.25 offers the best balance. Adjusting this threshold will encourage us to revisit the original dashboard and assess the changes—demonstrating how this quickly becomes an iterative process of continuous improvement.
How to Use This Framework
This approach enables a principled, data-driven method for guardrail selection:
- Deploy multiple guardrails in parallel with tracing enabled
- Feed in both adversarial and safe prompt datasets
- Analyze metrics for precision, recall, and latency
- Tune or disable underperforming guardrails
- Lock in guardrails that balance security with usability
No single guardrail is best, and what works well against encoded prompts may fail against emotional manipulation. Performance matters, and LLM safety tooling should not make your app unusable. Observability is key, and, without traceability, jailbreaks become invisible and guardrails become guesswork.
This framework gives you a repeatable process for testing, comparing, and justifying your safety architecture — so you don’t have to choose between security and speed, or reliability and user experience.
Guardrail Implementation Tips
Here are essential strategies that go beyond method type — these ensure your guardrail stack is reliable and complete.
- Check Input & Output: It is imperative that guardrails are set for both inputs and outputs. A prompt may look harmless but produce harmful content, so run guardrails before and after LLM generation.
- Add Output-Specific Guardrails: Consider the acceptable output for your LLM system and add additional checks. Check for leaked secrets or credentials, encoded payloads, unusually long or repetitive outputs (indicative of decoding exploits), and any other characteristics that would not be expected.
- Add Guardrails for File Uploads: If allowing users to upload documents, links, or chat history, ensure you guard against payload injection hidden in long documents, adversarial instruction examples, multi-shot prompting, etc.
- Normalize Inputs Before Guardrail Checks: Before checking prompts for violations, normalize inputs by stripping extra whitespace, correcting spelling, converting homoglyphs, decoding encoded text, and translating foreign languages.
- Prioritize Structural Guardrails Over Ethics Models: Social engineering exploits often target the model’s ethical alignment. Ensure system-level filters (topic, decoding, intent) run before values-based guardrails.
- Add Output Tracing: Embed identifiers (e.g. user IPs) in output traces to track repeated abuse attempts and flag suspicious users. With output tracing, you can easily pull successful jailbreaking attempts and add them to your existing database to train and adjust your guardrails to be stronger.
Final Thoughts
In the previous blog, we discussed how the most effective form of jailbreaking is combinatorial. Likewise, the most effective defense is a combinatorial approach to guardrails. No single filter or model can protect against the full spectrum of jailbreak strategies. But selecting and tuning the right guardrails isn’t easy. That’s where observability platforms like Arize come in. By providing real-time insights into prompt patterns, model behavior, and guardrail performance, Arize enables you to monitor, evaluate, and iterate quickly. With the right mix of techniques — from keyword bans and topic restrictions to LLM-based reasoning and robust feedback loops — you can move beyond reactive defenses and build systems that adapt to emerging threats over time.