Large language models are reshaping how we build products — and how adversaries try to break them. To help teams stay ahead, Sofia Jakovcevic — AI Solutions Engineer at Arize AI and an alumna of OpenAI — wrote this two-part guide on how jailbreaks really work and how modern guardrails can shut them down. Skim the highlights below.
Part 1: Jailbreaks
→ Read the complete guide for jailbreaking AI models
This concise deep dive distills months of red-teaming experience into an afternoon read.
Why you want this on your desk:
-
See the whole attack surface. From system-prompt leaks to file-upload prompt injections, the guide maps many popular components a red-teamer might exploit.
-
Learn the real tactics—not just the memes. Dozens of live jailbreak examples illustrate direct overrides, role-play exploits, emotional manipulation, multilanguage encoding, and combinatorial “ultimate” attacks.
-
Think like an adversary. By dissecting what makes each approach effective, you’ll spot weak points in your application before attackers do.
Part 2: Guardrails
Think of this sequel as the hands-on playbook that turns theory into repeatable guardrail practice.
Why this matters for production:
-
Defense in depth, explained. Compare keyword bans, topic filters, ML-based detectors, LLM-in-the-loop moderation, drift tracking, and more—side-by-side with trade-offs.
-
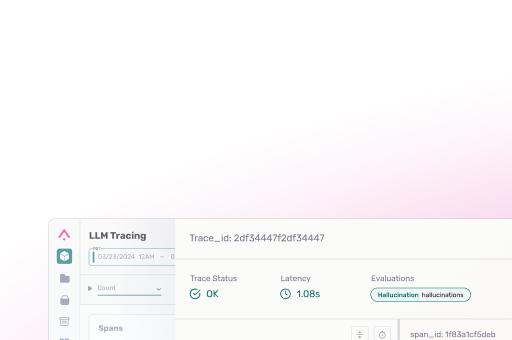
Observability = security. See how Arize traces each guardrail’s latency, precision, and recall so you can tune safety without tanking UX.
-
Plug-and-play framework. Get a GitHub reference repo on jailbreak guardrails plus dashboards that turn guardrail tuning into a repeatable, data-driven loop.
Next Steps
Master the offense, master the defense. Then ship with confidence.